Posts
 Photo by Brooke Cagle on Unsplash
Photo by Brooke Cagle on UnsplashSocial Engineering: Meaning and Impact
Claims Management, Cyber Liability Insurance, Line of Insurance, Loss Control, Risk ManagementDefinition
Social Engineering is the means of deception to extract sensitive, personal information that can then be used for further purposes, such as bank fraud, account takeovers, or identity theft. Cyber hackers primarily use social engineering…

Capital One Data Breach: Assessment and Prevention
Cyber Liability Insurance, Loss Control, Risk Management
Last year, after the Capital One Data breach, Capital One agreed to terms with US regulators to pay $80 million dollars in fines because of a data breach. The hacker accessed approximately 100 million credit card applications. Maintaining…

Cognizant Gets $400 Million Payout After Cyber Attacks
Claims Management, Cyber Liability Insurance, Loss Control, Risk ManagementTechnology consultant firm Cognizant fell victim to cyber-attacks caused by a ransomware attack last April. The hack disrupted thousands of employees from accessing networks from their home during quarantine. Clients also disallowed Cognizant…

Buying Cyber Insurance Does Not Protect Your Organization From Cybercriminals
Cyber Liability Insurance, Risk ManagementBuying Cyber Insurance Does Not Protect Your Organization From Hackers
Understand that purchasing Cyber Insurance does not protect your organization from hacking. It simply finances pieces of the loss. A recent report by cybersecurity…
 Photo by Christopher Gower on Unsplash
Photo by Christopher Gower on UnsplashConducting An Organization Wide Phishing Test
General Liability Insurance, Other
Remote operation of your business means that protections your office building had, your employees' homes may not. Cybercriminals are taking advantage of this situation by phishing out your employees' data. Take the time to educate your employees…
 Photo by Ilya Pavlov on Unsplash
Photo by Ilya Pavlov on UnsplashBusiness Interruption and Ransomware
Cyber Liability Insurance, Line of Insurance, Loss Control, Practice Groups, Risk ManagementRansomware is a type of malware designed to deny access to a person’s computer unless they pay the hacker ransom. The NY Times reports that these attacks have grown over the past year with a 41 percent increase in 2019. Ransomware attacks…
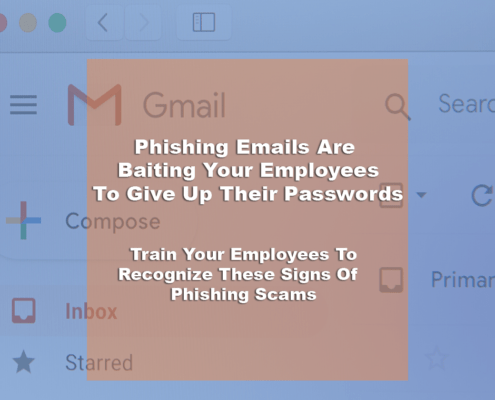
Phishing Attacks: Know the Signs!
Cyber Liability InsuranceBeware of Phishing!!!
Hackers will start with low-level employees first, making their way to executives’ accounts.
Hackers are constantly trying to find ways to hack into company accounts. They start off by sending trust-worthy emails…

Our SIM-Hacking Prevention Guide
Cyber Liability Insurance, General Liability Insurance, HR Challenges, Risk Management, VlogsWe recently wrote a piece about what SIM-Hacking or SIM-Swapping is. Click this link here to read it. We’re following up on that article with a quick guide to preventing SIM-hacking. We’re not here to re-explain what SIM-hacking is, we’re…
 Photo by Markus Spiske on Unsplash
Photo by Markus Spiske on UnsplashThe 21st Century Solution for Business Protection: Cyber insurance
Construction Practice Group Content, Cyber Liability Insurance, Food & Beverage Practice Group Content, General Liability Insurance, Human Services Practice Group Content, Line of Insurance, Loss Control, Practice Groups, Risk Management, Transportation Practice Group ContentOrdering a pizza, listening to music, getting a mortgage. All are examples of normal activities that have adapted with the emergence of computers. It is no wonder that insurance has also taken part in this advancement into the new era. However,…
