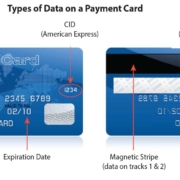
We recently wrote a piece about what SIM-Hacking or SIM-Swapping is. Click this link here to read it. We’re following up on that article with a quick guide to preventing SIM-hacking. We’re not here to re-explain what SIM-hacking is, we’re here to talk about how to protect yourself from risk.
1. Make a list of the important stuff that would pain you if you were hacked.
Here are a few accounts to start with. Your list of accounts to protect may grow longer but these accounts would be the most problematic.
- Work Email/ Work Google Account
- Bank Account for Work or Personal
- Organizational/Workplace Databases
- Social Media Accounts (Facebook, Linkedin & Vimeo)
2. Understand how each account lets you recover/reset your password.
In this case, each one uses 2-step verification. The first factor is typically the primary email address you used to set up the account. The second factor is your mobile phone number (text messaging). I suggest testing each account above to have them bring you through the steps of a password reset. The ones that send a text message to your mobile phone are the ones that are most vulnerable to SIM-HACKING as that is the purpose.
These are the accounts we are going to lock down in the next few steps.
How To Protect Yourself From SIM-Hackers
At Metropolitan Risk, we purchased a YUBIKEY, which is a small piece of hardware that replaces the text message/cellphone as a second level authenticator. Google offers a similar product known as the Titan Security Key. We opted to use a security key because you must have the key in your physical possession and you must confirm to the hardware that you are a human being. These security keys require human touch to confirm and cycle the key on. If you don’t like the idea of a separate piece of software, there are some apps on your cellphone called Authenticators that can do similar things.
We opted for a separate piece of hardware to the cellphone as a 2nd step in the 2-Step Verification. We do use an authenticator as a 3rd level authentication process in the event we lost the YUBIKEY hardware.
1. If you’ve purchased a YUBIKEY, your next task is to log into the accounts you are concerned about & research the multi-step authentication process for password recovery.
-
- This is the most time-consuming part of the process as each account can have different methods & steps to execute this piece.
For Example, you are telling Google not to send a text message to your cellular phone. Instead, you are telling Google to look for your YUBIKEY as the primary authentication.
- This is the most time-consuming part of the process as each account can have different methods & steps to execute this piece.
NOTE: that if your organization manages your email account, that you speak with your admin. As our google account administrator, I’ve turned on 2-step verification to allow my staff to use yubikey. My staff would not have been able to set this up without admin approval. CLICK HERE for a quick guide for Google as an example on how to execute 2 step authentication as an example.
2. Once you follow the instructions for linking your account with the YubiKey you can select “trust this device”. This way you won’t need to use the YubiKey every time you log into an account because the software recognizes your device AND it has been properly authenticated.
What Happens if I lose my YubiKey?
In all the accounts you set up with the Yubikey make sure there is a 3rd way to authenticate in case the YubiKey isn’t available for some reason. This gives you an additional way to access your account and prevents you from getting locked out of say your google account. In our case, we use Google Authenticator as the 3rd option in case the Yubikey is damaged or otherwise unavailable.
Call me paranoid, or maybe just a Risk Advisor… same thing. I purchased a TILE which is essentially a very small chip that allows me to always locate whatever the chip is attached to. I have one for my wallet, one for my keys and one for my backpack. You download an app onto your cell phone. The cell phone app communicates with the tile which is attached to your keychain/YubiKey and voilà, keys found. It can also reverse and help you find your cellphone by making it ring if you press a button, even when the sound is on mute for the phone.
Help and More
At this point, I’m feeling better about my personal situation.
The 2-step verification ensures that the person accessing your account on a new device is you. Remember, once a hacker obtains your user name and password, they try to access your account from devices that are not recognized by the site or software. The software is trying to figure out if it is really you on a completely different account or a hacker. If the hacker has some way to authenticate their device to trick your software that it is you behind the device, they aren’t getting in.
Last point, just like in the physical world. If they really want to steal your car…gone. By locking down your digital life and making it a bit more difficult, the hackers usually move on to easier prey. Then, there is no shortage of easy prey out there.
We hope you found this helpful. There are a ton of resources online to execute this tactic to lock down your accounts and your life. Our goal was simply to make you aware of the SIM-Hacking. At least get you to start the process of locking down your very vulnerable digital life.
Still have questions? Still want more info? Contact a risk advisor today OR visit our website here.



 Photo by Christopher Gower on Unsplash
Photo by Christopher Gower on Unsplash